Law Is Complex, but Legal Software Shouldn’t Be
Great lawyers need Bloomberg Law to win
Make your legal team more productive with trusted news, primary and secondary sources, practice tools, and expert legal analysis — all in one place, for one price.
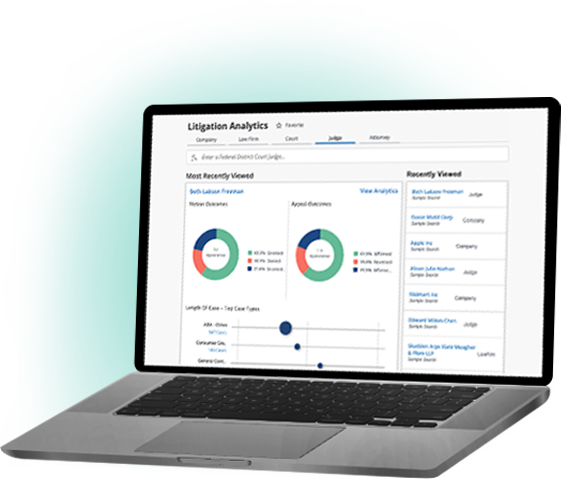
Bloomberg Law: Built for lawyers, by lawyers
We combine deep legal expertise with innovative, cutting-edge technology to deliver the news, analysis, and legal tools you need to speed your workflow. Deliver a winning strategy with Bloomberg Law’s all-in-one legal platform.
Work without limits
Switch to a legal intelligence platform that has everything you need in one convenient suite.
Stay sharp
Find all the latest legal updates from sources you can trust with 40+ news channels, the Bloomberg Terminal, and ALM Media News.
Practice smarter
Rely on our legal tech tools to optimize your time and speed up daily tasks.
Legal teams trust Bloomberg Law
With legal expertise powered by Bloomberg’s advanced technology, our platform helps the nation’s leading legal teams simplify how they stay ahead of the curve.
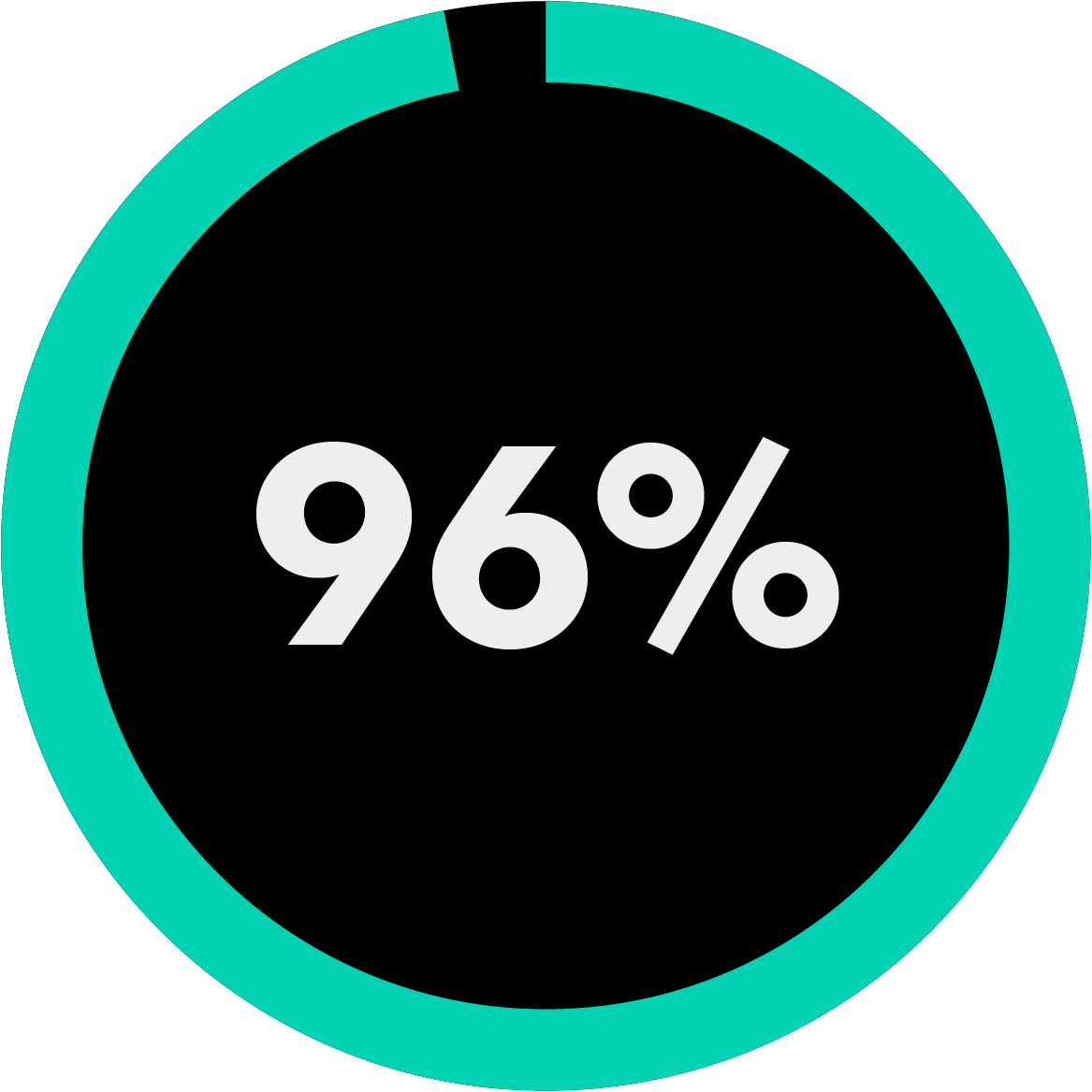
of the Am Law 200 firms use Bloomberg Law

of federal circuit courts use Bloomberg Law
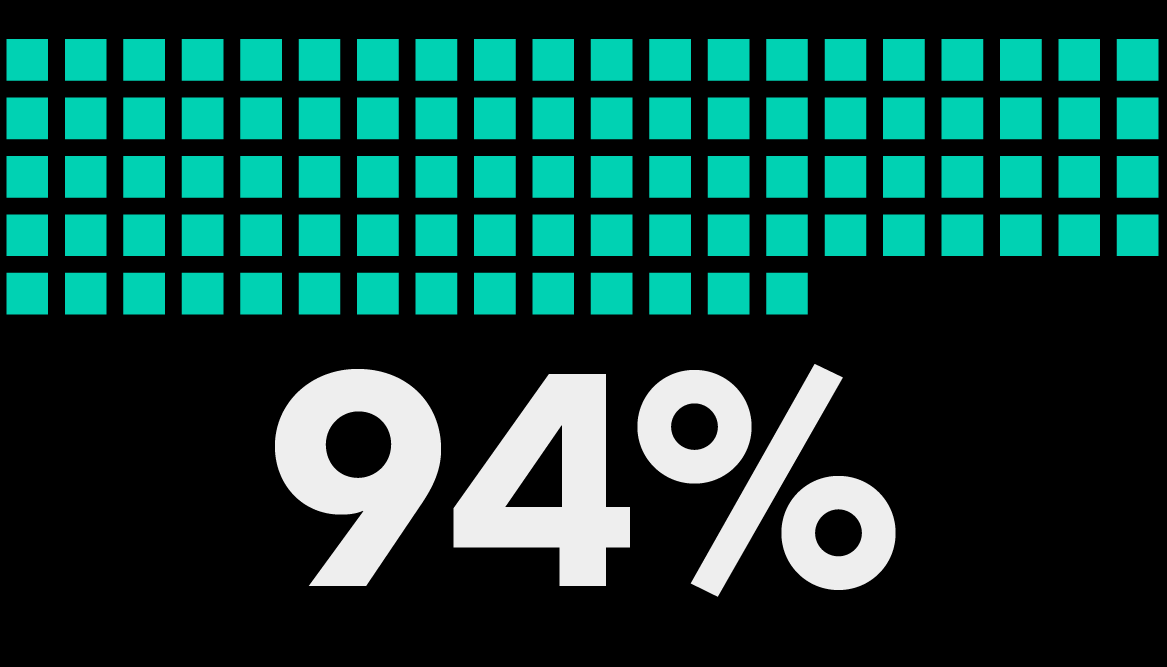
of GCs and CLOs agree that Bloomberg Law has the tools they need
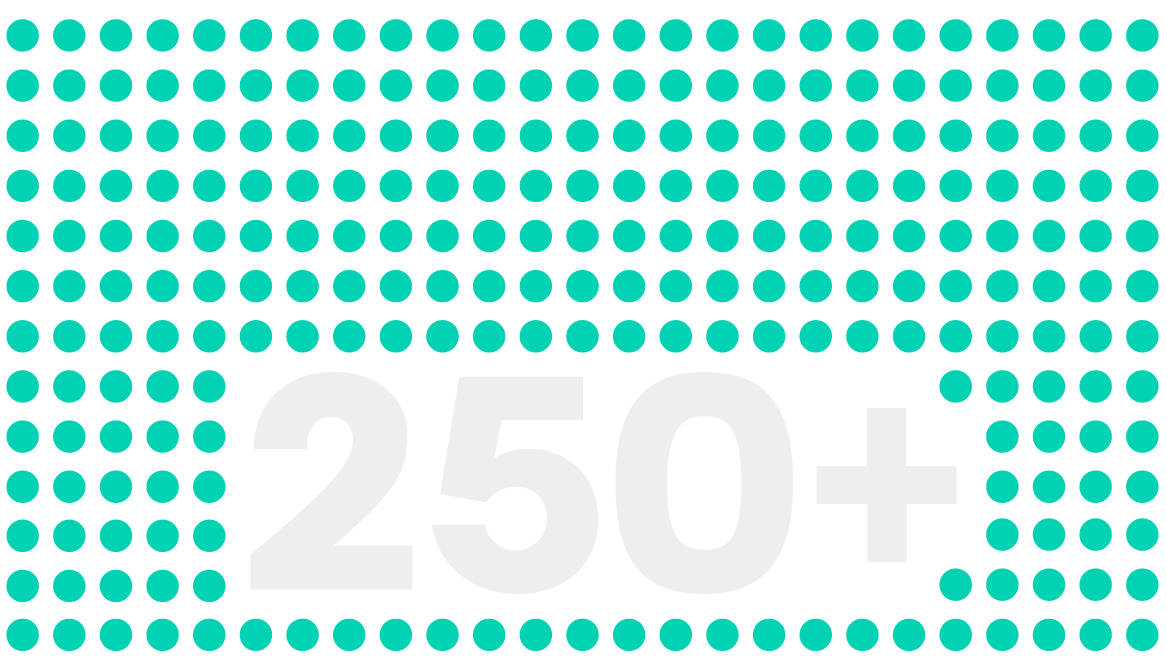
reporters delivering stories you can trust
What’s the verdict?
“The Chart Builder tool allows me to see the relevant statutes for multiple states with one click. If I had to locate those statutes individually, the time it takes would be multiplied by the number of jurisdictions involved. So it would take anywhere from two to 10 times as long.”
Laura Greer
General Counsel
Ennis-Flint, Inc.
“Dockets are probably the reason we got the product firmwide. Our litigation practice is such that we needed really deep litigation research capability, and this ability to really scan a docket at a very, very granular level is unique to Bloomberg Law. Nobody else can do it.”
Ed Brandwein
Head Librarian
Patterson Belknap Webb & Tyler
“Bloomberg Law has the most comprehensive content for my work, and the flat, all-inclusive pricing means I can use tools occasionally that I would not otherwise use without incurring additional expense.”
Practice Area Leader
Small Law
Designed to sharpen any legal team
Find out how Bloomberg Law can be the all-in-one legal platform for your organization’s needs, whether you’re part of a law firm, in-house counsel, government, or law school.
Insights
Request a demo
Bloomberg Law is the all-in-one legal platform that’s remarkably simple to use and gives you everything you need to win.
Complete the form and a representative will contact you to schedule a demo. The demo will provide an overview of our latest features and an inside look into our platform.
All fields with an asterisk (*) are required.
Already a customer? Get in touch with the support team.